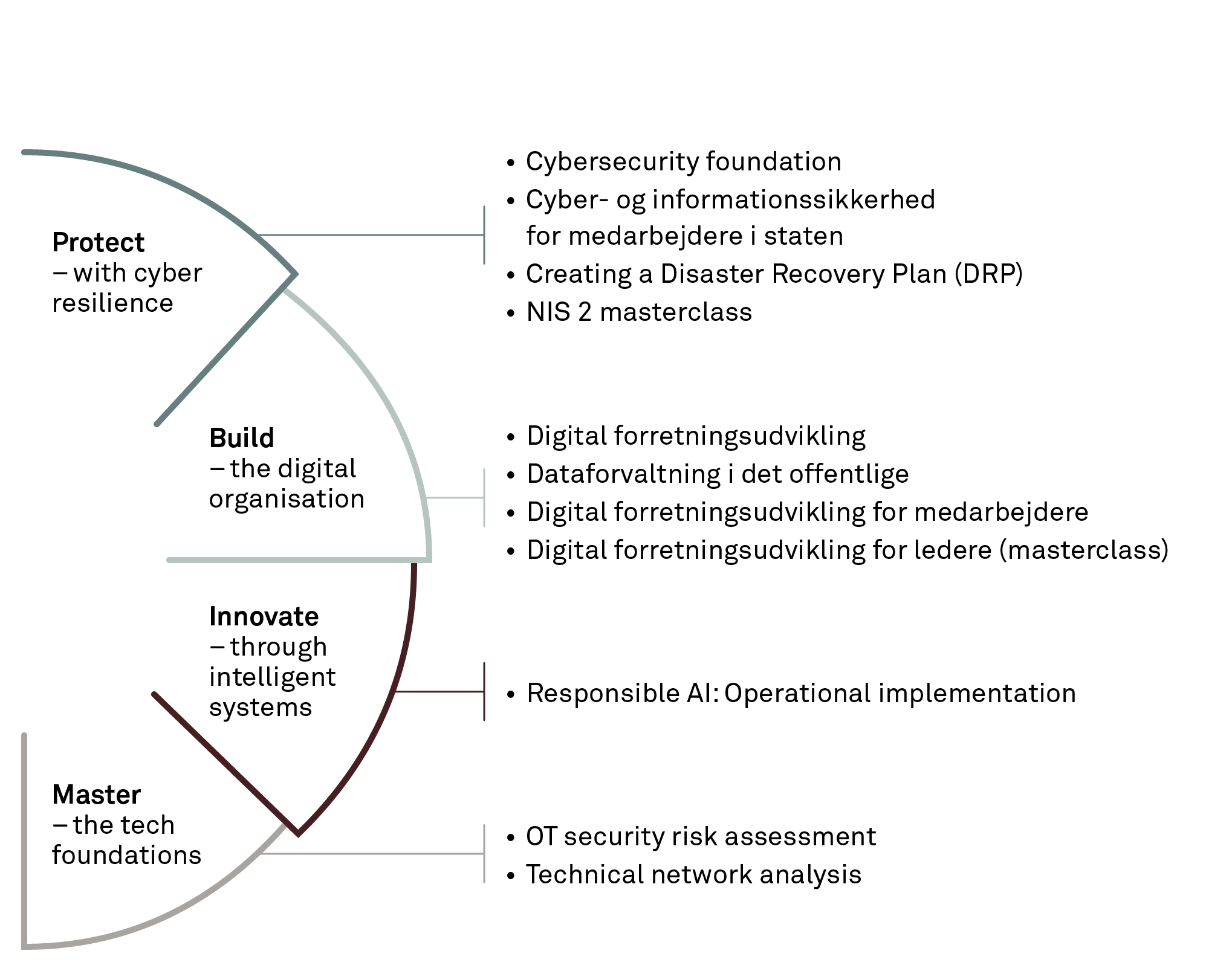Purpose of the course
To stay ahead of modern threat actors, defenders must apply network and forensic capabilities, monitor for and detect cyber threats, deconstruct cyber attacks to extract lessons learned, perform incident response, and take an intelligence-driven approach to ensure safe and reliable operations.
By the end of this course, your IT or security department will be equipped to:
- Detect anomalies in network traffic.
- Generate actionable threat intelligence.
- Strengthen incident response capabilities.
- Build a practical and theoretical baseline
What you will get from participating in this course
The course seeks to arm participants with the core skillset needed to perform active cyber defense. You will learn:
- The cyber kill chain and threat modelling
- Networking 1-0-1 and network traffic analysis.
- The skills needed to dissect and analyze network traffic.
- The protocols that makeup today’s internet.
- Encryption, basic cryptography and eavesdropping techniques.
- To understand and conceptualize the impact from cyber attacks.
- Open-source intelligence and investigation techniques.
- How to piece technical findings together and produce actionable threat intelligence reporting.
Participants
Employees engaged in operational or technical roles with NIS2 or the Digital Operational Resilience Act (DORA).
Former compliance employees now in technical or operational roles.
Individuals motivated to increase their understanding of network analysis.